4.1 INTRODUCTION
 The basic principle of “Double Entry System (DES)” is to provide a mechanism to increase the accuracy of the deliverables during the entire data processing cycle by sacrificing time and cost in providing a second typing process.
The basic principle of “Double Entry System (DES)” is to provide a mechanism to increase the accuracy of the deliverables during the entire data processing cycle by sacrificing time and cost in providing a second typing process.
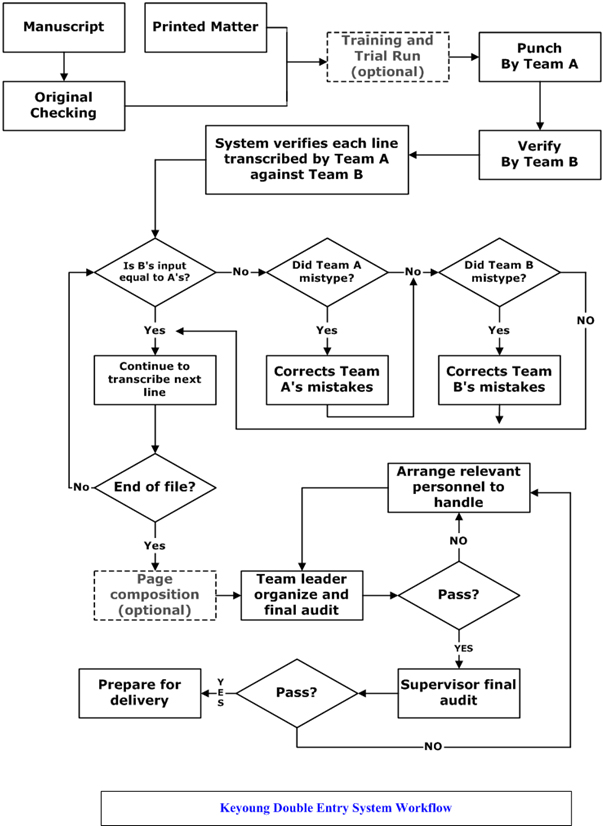
Double Entry or “Punch and Verify”, is a technique we employ to achieve guaranteed accuracy rates of 99.92%or greater for printed matter documents. The same data is punched and verified by two different operators. Where there is any mismatch between the two operators, the system will stop and let the second operator examine the original document again and then make appropriate corrections. This scientific approach will dramatically increase accuracy and virtually eliminate the drawbacks from manual proofreading. Finally, a data quality auditor will conduct a random 5% quality check of the data capture results.
The following will illustrate this system with examples.
We have the following parties: D – the document to be typed M – the maker (the first typing person) C – the checker (the second typing person who serves also the verification person)
Accuracy is measured by referring to D. Anything typed different with D will be regarded as an error.
In real life, M may make mistakes and C may also introduce mistakes. We do not trust M and we do not trust C as well. The beautifulness of the DES is to ensure that we trust the result from C by letting C following the proper workflow. In this case, we need not have sophisticated management involvement to judge M and C’s discipline.
The design is to let C use M’s result plus referring to D to correct both M’s and C’s mistakes if any. This is the most cost-effective way to ensure accuracy without introducing a third party.
Another more expensive approach is to introduce a third party called the Judge (J) to check the difference that M and C made and then correct the mistakes made by either M or C by referring to D. DES is proven as a feasible working model for providing accurate data entry service.
4.2 THE MECHANISM
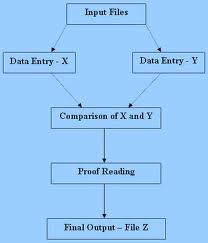 Let’s illustrate by using the following example:
Let’s illustrate by using the following example:
Now M and C are going to type D below:
D = 28/F Data Processing Center
Case 1: M is incorrect and C is all correct:
M = 28/F Date Processing Centre
C = 28/F Data Processing Center
C knows the following facts by looking at M’s result:
(1) There are 3 places that M and C are different (2) The other characters are correct. This is very important! Without seeing M’s result, C will never know which are correct and which are the suspected ones.
C will then focus on the above 3 places ONLY by referring to D and correct M’s result. This is also very important! If C needs not correct M’s error, we will never know if C has actually referred to D!
You can say if C does not refer to D even if he knows that there is a discrepancy between M and C, then it should be C’s discipline problem and can be solved by using management techniques. But without letting C to correct M’s incorrect data, you do not have any proof to say that C does not refer to D. C may or may not refer to D. This design is to let us trust the system instead of the people. C needs actually did something and we trust the fact that C has referred to D. That “something” is trying to correct M’s incorrect data.
C can proceed to the next field if M’s typing equal to C’s typing. You will say how about if C copies M’s result and then proceed. Yes, this is the discipline problem and the management will take appropriate action. Actually, in our system, we will keep M’s original typing result and C’s modification on M’s result is just a copy of it. In this case, it is easy to find if C is doing the “copy” trick. When C knows that his copy trick will be easily detected if the management wants to do so, C will not intend to do so.
Case 2: M is all correct and C is incorrect:
M = 28/F Data Processing Center
C = 28/F Date Processing Centre
C knows the following facts by looking at M’s result: (1) There are 3 places that M and C are different (2) The other characters are correct. This is very important! Without seeing M’s result, C will never know which are correct and which are the suspected ones.
C will then focus on the above 3 places by referring to D and correct C’s result. When both match, the system will let C proceed to the next field.
Case 3: M is incorrect and C is incorrect too:
M = 27/F Data Processing Center
C = 28/F Date Processing Centre
C knows the following by looking at M’s result: (1) There are 4 places that M and C are different (2) The other characters are correct. This is very important! Without seeing M’s result, C will never know which are correct and which are the suspected ones.
C will then refer to D and correct both M’s errors and C’s errors. The system will let C proceed if both M’s result and C’s result are equal.
The only error that DES cannot detect is when M and C are making the error at the same place but this is acceptable as this chance is rare and is within the acceptable error rate range.
Case 4: M is all correct and C is all correct too
In this case, the system will just let C proceed to the next field without showing any of M’s result.
4.3 SUMMARY
 The following points are very important in the entire DES:
The following points are very important in the entire DES:
(1) The system must highlight the difference between M and C’s results so that C can concentrate on the difference and make appropriate corrections. This is to save C’s time and improve efficiency.
(2) The system should not let C proceed if both results do not match. This is to ensure that C will REALLY look at D again and make proper corrections no matter who made the mistakes.
(3) C is responsible for correcting both M’s and C’s errors. C is using M’s result to prove himself right for the matching characters and correct those unmatching characters.
(4) The system shows M’s result only when there is any difference with C’s. The difference must be highlighted properly. C should only focus on the difference as the others are already correct and needs no special handling.
4.4 Keyoung Double Entry System Workflow